Decrypt Keychain.plist
For this u need to create a 'autorun.inf' file in ur pendrive, and copy paste the contents as follows:
[AutoRun]
icon=iconsiconname.ico <---------path to ur icon
label=Saurabh's PD <---------name of ur PD
ShellOption1Command=Softwareanything.exe <---------path to software to run after autorun
If u dont have .ico file and u want to change ur .jpg file to .ico .Link to this:
http://www.prodraw.net/favicon/generator.php
Enjoy with ur customized Pendrive...
Apr 11, 2012. This post details the step-by-step method required to extract a plist/OAuth token from a standard (non encrypted) iTunes backup of any iOS device. IOS backups and avoid connecting your iOS device to any computers other than your own until the app developers re-write their apps to use keychain stores. Property lists, or plists, can contain data key-value pairs, which are binary property list files encoded in Base64. Here's how to decode data plist.
Is it possible to decrypt the keychain data from ios 12.1 from a keychain-backup.plist file? The phone was wiped so it was extracted from a recent backup. This thread is archived. New comments cannot be posted and votes cannot be cast. What is plist Editor Pro? In the Mac OS X and iPhone OS, property list files are files that store serialized objects. Property list files use the filename extension.plist. Computerworld covers a range of technology topics, with a focus on these core areas of IT: Windows, Mobile, Apple/enterprise, Office and productivity suites, collaboration, web browsers. Keychain encrypts the stored passwords and credit card numbers with 256-bit AES, which is one of the most advanced encryption standards available. The facility also employs end-to-end encryption tech and works to provide a device with a unique key and passcode. Only the user is supposed to know the passcode used to access keychain. –Clear text / Weak encryption –Client-side attacks.The web server.Assess data sources (keychain, plist files, cookies).Check presence of caching.

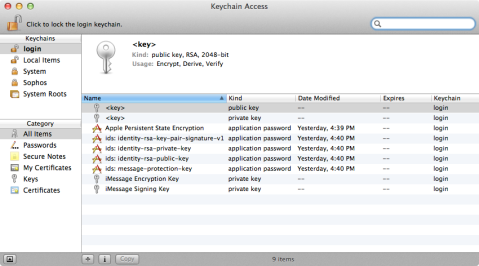
Decrypting the Keychain Once the device encryption keys have been recovered using the KeyTheft payload, and the device’s filesystem has been recovered using the DataTheft payload, you have everything you need to decrypt passwords stored on the device’s keychain. The decryption process can be performed on the desktop, and so unless you’re performing other tasks with the device (such as decrypting raw disk), the device is no longer needed. An attacker could execute both payloads (or a single, combined payload to obtain both the keychain and the keys) within only a minute or two, with practice. If you haven’t already done so, extract the tar archive you obtained from the device using the DataTheft payload in.
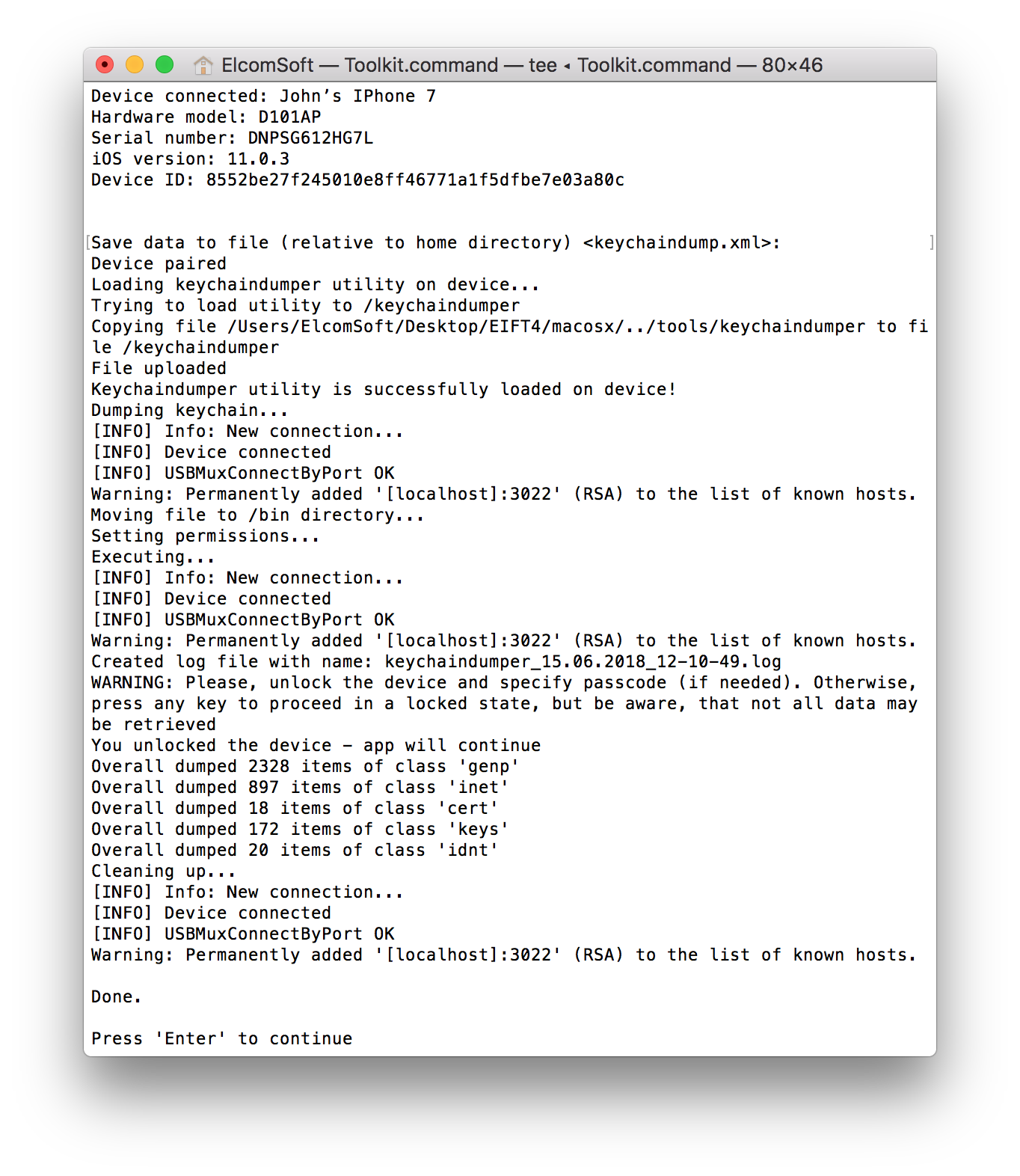
Decrypt Keychain-backup.plist
Find the file private/var/Keychains/keychain-2. Download Autodesk Inventor Professional 2013 Full Crack. db and copy this to the same directory as the DeviceEncryptionKeys.plist file you obtained using the KeyTheft payload. $ tar -xf filesystem.tar $ ls -l private/var/Keychains/keychain-2.db In a terminal window, change into Sogeti’s tools’ python_scripts directory. You will find a script named keychain_tool.py.
Decrypt Iphone Keychain-backup.plist
Run this script with the path to the keychain-2.db file you extracted from the filesystem dump. $ python keychain_tool.py -d keychain-2.db DeviceEncryptionKeys.plist The script will display all records stored on the device’s keychain, including clear text copies of the passwords stored. The keychain can hold website passwords and application credentials used to log into various accounts or websites, and is even sometimes. With Safari, you learn the way you learn best. Get unlimited access to videos, live online training, learning paths, books, interactive tutorials, and more.