Anticloud 2018 Rev 4
SP 800-53 Rev. 4
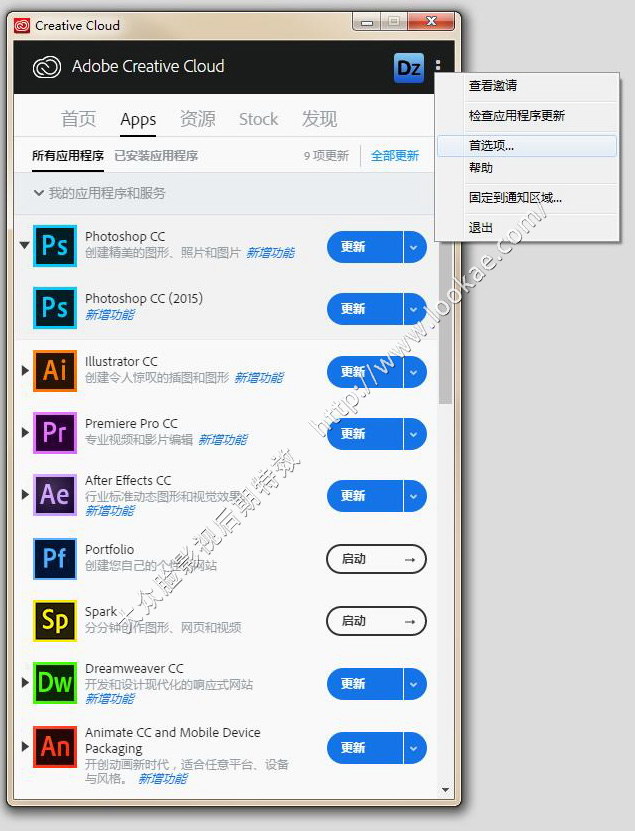
DE 4 Rev 50 (1-21) (INTERNET) EMPLOYEE’S WITHHOLDING ALLOWANCE CERTIFICATE Complete this form so that your employer can withhold the correct California state income tax from your paycheck. Enter Personal Information First, Middle, Last Name Social Security Number. City, State, and ZIP Code. SINGLE or MARRIED (with two. 添加支持2018.4月份更新 – 2017年10月25日发布 Anticloud Rev.3 增加对 Adobe XD 软件的破解 – 2017年10月19日发布 Anticloud Rev.1.
Adobe.CC2018.Anticloud.r4.exe共收录25个同名文件,其中安全0个,不安全25个,100%可能是病毒 - VirSCAN.org - 온라인 무료 바이러스 검사 서비스.
Date Published:April 2013 (Updated 1/22/2015)
Superseded By:SP 800-53 Rev. 5 (09/23/2020)
Supersedes:SP 800-53 Rev. 4 (01/15/2014)
Planning Note (9/23/2020):This publication was superseded by SP 800-53 Rev. 5 on September 23, 2020. Revision 4 will be officially withdrawn in one year, on September 23, 2021.
Author(s)
Joint Task Force Transformation Initiative
Abstract
This publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation from a diverse set of threats including hostile cyber attacks, natural disasters, structural failures, and human errors (both intentional and unintentional). The security and privacy controls are customizable and implemented as part of an organization-wide process that manages information security and privacy risk. The controls address a diverse set of security and privacy requirements across the federal government and critical infrastructure, derived from legislation, Executive Orders, policies, directives, regulations, standards, and/or mission/business needs. The publication also describes how to develop specialized sets of controls, or overlays, tailored for specific types of missions/business functions, technologies, or environments of operation. Finally, the catalog of security controls addresses security from both a functionality perspective (the strength of security functions and mechanisms provided) and an assurance perspective (the measures of confidence in the implemented security capability). Addressing both security functionality and assurance helps to ensure that information technology component products and the information systems built from those products using sound system and security engineering principles are sufficiently trustworthy.
This publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation from a diverse set of threats including hostile cyber attacks, natural disasters, structural failures, and human errors (both intentional and unintentional). The security and privacy controls are customizable and implemented as part of an organization-wide process that manages information security and privacy risk. The controls address a diverse set of security and privacy requirements across the federal government and critical infrastructure, derived from legislation, Executive Orders, policies, directives, regulations, standards, and/or mission/business needs. The publication also describes how to develop specialized sets of controls, or overlays, tailored for specific types of missions/business functions, technologies, or environments of operation. Finally, the catalog of security controls addresses security from both a functionality perspective (the strength of security functions and mechanisms provided) and an assurance perspective (the measures of confidence in the implemented security capability). Addressing both security functionality and assurance helps to ensure that information technology component products and the information systems built from those products using sound system and security engineering principles are sufficiently trustworthy.
 Hide full abstract
Hide full abstract
Keywords
FIPS Publication 200; FISMA; Privacy Act; Risk Management Framework; security controls; FIPS Publication 199; security requirements ; ; computer security; assuranceControl Families
Access Control; Audit and Accountability; Awareness and Training; Assessment, Authorization and Monitoring; Configuration Management; Contingency Planning; Identification and Authentication; Incident Response; Maintenance; Media Protection; Personnel Security; Physical and Environmental Protection; Planning; Risk Assessment; System and Communications Protection; System and Information Integrity; System and Services Acquisition
Documentation
Publication:
SP 800-53 Rev. 4 (DOI)
Local Download
Supplemental Material:
Word version of SP 800-53 Rev. 4 (01-22-2015) (word)
800-53 Rev 4 Control Database (other)
XML file for SP 800-53 Rev. 4 (01-15-2014) (other)
Summary of NIST SP 800-53 Revision 4 (pdf)
Press Release (04-30-2013) (other)
Other Parts of this Publication:
SP 800-53A Rev. 4
Related NIST Publications:
NISTIR 8170
NISTIR 8011 Vol. 3 (Draft)
SP 800-53A Rev. 4
SP 800-171A
NISTIR 8011 Vol. 3
SP 800-171A (Draft)
White Paper
White Paper
NISTIR 8011 Vol. 1
NISTIR 8011 Vol. 2
NISTIR 8170 (Draft)
Document History:
01/22/15: SP 800-53 Rev. 4 (Final)
Topics
Security and Privacy
acquisition; audit & accountability; authentication; awareness training & education; contingency planning; incident response; maintenance; planning; privacy; risk assessment; threats; vulnerability management
Anti Cloud 2018 Rev 40
Applications
communications & wireless
Anti Cloud 2018 Rev 4 Reviews
Laws and Regulations
E-Government Act; Federal Information Security Modernization Act; Homeland Security Presidential Directive 12; Homeland Security Presidential Directive 7; OMB Circular A-11; OMB Circular A-130